The government has awarded a contract to a multinational weaponry and defence firm to support policing and other authorities in their monitoring of UK citizens’ internet records.
But the company concerned is no stranger to mass surveillance. Moreover, p.
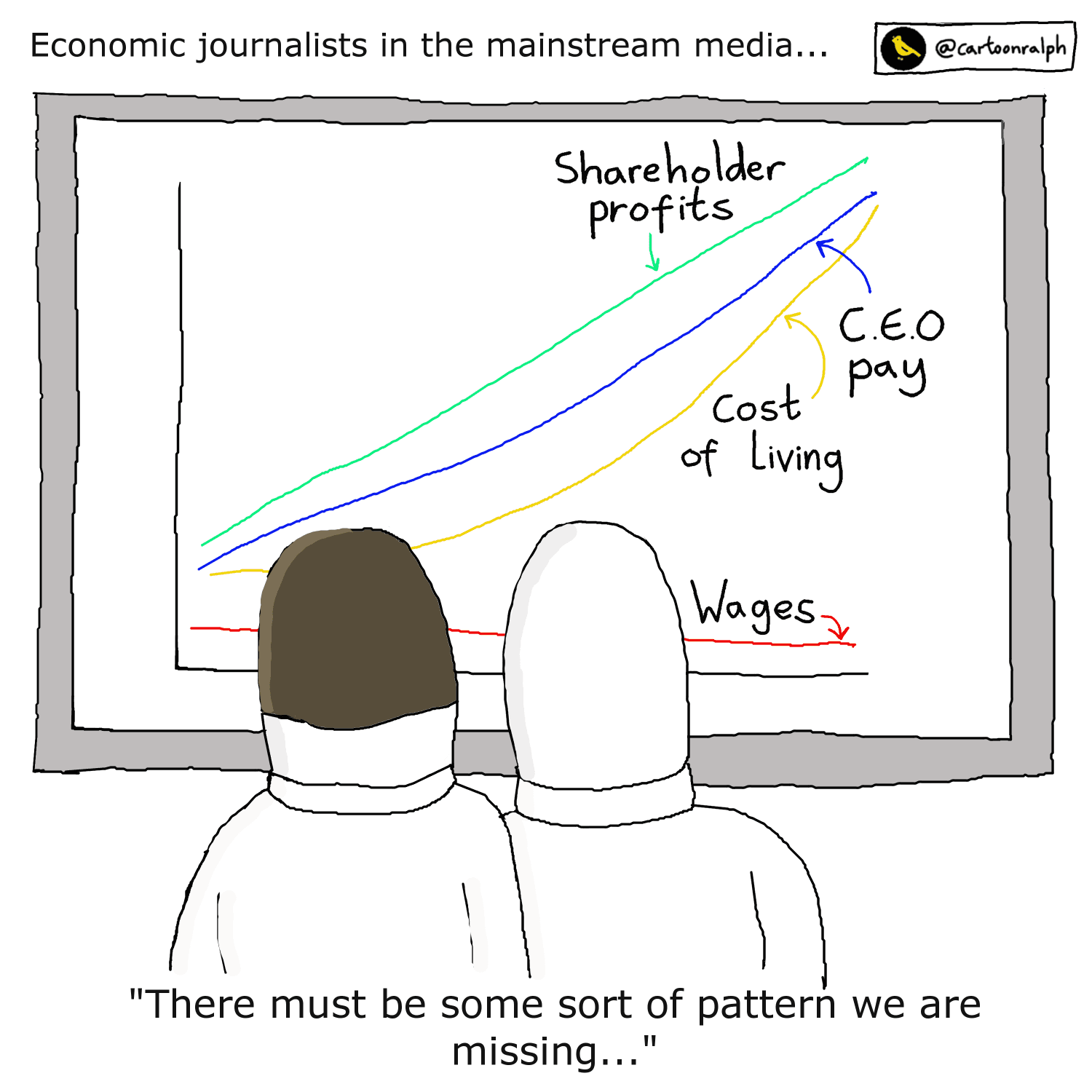
BAE contract
Public Technology reports that the National Communications Data Service (NCDS) has awarded a £2m contract to BAE Systems Digital Intelligence. NCDS comes within the Home Office’s counter-terror operations. BAE will provide “a means for law-enforcement agencies to search and, ultimately, gain access to data on individuals’ internet connection records (ICR)”.
The publication explains:
While an ICR does not provide a full browsing history including individual webpages, it contains information on all sites visited or apps accessed by a user, as well as details of the device used and the time and date of the visit. A user’s IP address and their customer account information with the telecoms provider in question is also embedded in the records.
According to a November 2019 procurement notice, NCDS utilises what it calls Agile Data Retention and Disclosure Services (ARDS), which comes under the Office for Security and Counter-Terrorism.
ARDS is essentially:
the ability to identify and locate subjects of interest and determine what, how and when they are communicating through the acquisition and exploitation of CD [communication data] and intercepted data.
The procurement notice adds that ARDS:
has obligations under the Investigatory Powers Act 2016 [IPA, aka “Snoopers Charter”] and the Communications Data Code of Practice whilst the [Telecommunication Operators] have obligations that are mandated via the data retention notice, ‘Investigatory Powers Act’ and the ‘IPA Code of Practice’.
In May 2022, Public Technology reported that a filtering tool to enable policing authorities to search for information would be “migrated into a datacentre storage provided to NCDS by Amazon Web Services”.
BAE spying
However, BAE also has its own track record of spying on campaigners and activists.
In May 2021, The Canary reported how freelancer Paul Mercer was exposed in 2007 for his ops on Campaign Against Arms Trade (CAAT). His contract was via private surveillance firm Global Open (GO). Mercer also worked as a security consultant for LigneDeux Associates, which was financed by BAE to provide information on ‘threats’.
Corporate spy Martin Hogbin infiltrated CAAT. He worked for Evelyn le Chêne and her company Threat Response International (TRI), which was contracted by BAE. Consequently, BAE was able to build a collection of files on activists. Hogbin was outed as a spy in 2003 while still employed as campaigns coordinator at CAAT.
More BAE surveillance projects
The NCDS contract isn’t the only government surveillance work undertaken by BAE. According to a CAAT report, A very British problem: The Evolution of Britain’s Militarised Policing Industrial Complex, BAE is a:
Top UK arms company, now expanded into policing, security and surveillance technology.
This includes the Home Office Biometrics programme that:
the government is attempting to merge the National DNA Database (which holds the DNA profiles of subjects in criminal cases), IDENT1, and IABS into a single, centralised platform. UK arms company BAE Systems, US company Leidos, and Indian multinational Mastek have all been involved in its The Home Office implementation.
The report notes that, if successful:
the initiative will increase the surveillance powers of the British state by enabling more government agencies access to biometric data.
Meanwhile, via ETI, its Danish subsidiary, BAE has:
exported a system known as Evident, which allows ‘governments to conduct mass surveillance of their citizens’ communications’. Capable of analysing millions of people’s electronic communications, Evident can be used to pinpoint a person’s location based on their mobile phone data and intercept their internet traffic.
Other privatised surveillance projects
Of course, surveillance projects involving government-corporate collaboration are not new.
For example, in November 2014 Channel 4 News found evidence that GCHQ was working closely with Cable and Wireless (subsequently taken over by Vodaphone) on monitoring internet traffic. This was done via GCHQ’s “Mastering The Internet” project:
Other telecom firms, including BT, partnered with GCHQ via the Tempora system, which “stores the collected data in a buffer to enable retrospective analysis”.
Wider surveillance
However, that’s only part of the story.
The Investigatory Powers Commissioner’s Office (IPCO) provides examples of surveillance covered by the IPA. These powers ensure that the UK is among the most surveilled countries in the world.
IPCO also reveals there are more than 600 public authorities that can utilise covert investigatory powers via the Regulation of Investigatory Powers Act (RIPA).
Wider investigatory powers include the use of covert human intelligence sources [CHIS]. The Canary reported that there are extensive bodies who can authorise CHIS agents to infiltrate or act as informants. They can include: victims, witnesses, suspects, colleagues such as local and field intelligence officers, community sources including community and race advisers, local councillors, religious leaders and members of the community.
CHIS was legalised in 2021 through the Covert Human Intelligence Sources (Criminal Conduct) Act. That legislation potentially sets citizen against citizen, in that anyone can be authorised to be an intelligence source (spy).
Illegal made legal
In 2015 the Investigatory Powers Tribunal (IPT) ruled that British intelligence services had in retrospect acted unlawfully in accessing millions of people’s personal communications.
In that same year the Interception of Communication Commissioner’s Office published a report that revealed how 19 police forces in Britain, over a three year period, made more than 600 applications to uncover 242 confidential sources and 82 journalists (mainly national newspapers). The report ruled that the police contravened Article 8 (right to privacy) of the European Convention on Human Rights and gave no consideration to journalists’ rights under Article 10 (freedom of expression).
In 2016, the IPT ruled that MI5, MI6, and GCHQ had been collecting data without supervision or safeguards. In 2018, there was another setback for the government when the European Court of Human Rights ruled that though UK surveillance operations were not illegal, they “violated the right to privacy as there wasn’t enough oversight for how data was collected”.
The IPA was an attempt to legalise some of these illegal practices. Bernard Keenan, a lecturer in law at Birkbeck, University of London summarised how the UK state deals with these legal challenges:
Everything that was revealed by Snowden,GCHQ, Tempora, Upstream… None of those capacities have diminished. What’s happened is that the law now makes transparent a large amount of what the authorities were doing anyway. But the mass surveillance regime has not changed – at the best, you can say that the oversight regime has been enhanced.
Resist
The BAE contract is further proof that government departments and policing agencies are happy to continue spying on its citizens by collaborating with a private company that has a history of surveillance of political activists.
We need to resist this extensive intrusion into our lives. To some extent citizens can protect themselves from state and private online surveillance by following this advice from Edward Snowden.
If we don’t, the alternative is total surveillance and an all-powerful, all-seeing state.
Featured image via Pixabay / Gerd Altmann cropped 770×403 pixels